Symantec Endpoint Protection (Activation number included)
Last Updated:2-07-2024, 08:01
Symantec endpoint protection download
About
Step into the digital age with confidence, knowing that your devices and data are shielded from relentless cyber threats. Welcome to the ultimate safeguard, where seamless protection and unparalleled security converge. Venture into the realm of unwavering digital defense and enter a world where your worries vanish.
Symantec Endpoint Protection Download
Protect your devices from cyber threats with our cutting-edge cybersecurity solution, available for immediate download.
Comprehensive Device Security
Shield your computers and mobile devices from viruses, malware, ransomware, and other malicious attacks. Our advanced threat detection and response capabilities ensure robust protection against evolving cyber threats.
Seamless Integration
Effortlessly integrate our solution into your existing network infrastructure. The intuitive interface simplifies setup and management, minimizing disruption to your workflows.
Stop Cyber Threats with Symantec Endpoint Protection
In a constantly evolving digital landscape, malicious actors are relentlessly exploiting vulnerabilities and launching devastating cyberattacks. Safeguard your organization from the incessant onslaught with Symantec Endpoint Protection.
Comprehensive Protection for Your Endpoints
Shielding your digital frontiers is paramount in today's interconnected realm. Every device connected to your network presents a potential entry point for malicious threats. Our comprehensive protection suite fortifies your endpoints, encompassing workstations, laptops, servers, and mobile devices, with an impenetrable barrier against cyber threats.
Securing Your Data and Devices
In today's digital age, safeguarding your sensitive data and devices is of paramount importance. With the proliferation of cyber threats and potential vulnerabilities, it has become essential to implement comprehensive security measures to protect your information and assets from unauthorized access and malicious attacks.
Protect Your Data
Your data is an invaluable asset that requires robust protection. Our advanced security solutions offer multiple layers of protection to safeguard your sensitive information from phishing, ransomware, and other cyber threats. We employ industry-leading encryption technologies to ensure your data remains confidential and protected from unauthorized access.
Safeguard Your Devices
Your devices are portals to your personal and professional life. We provide comprehensive device protection that shields your computers, laptops, smartphones, and tablets from a wide range of online threats. Our advanced anti-malware and intrusion detection systems identify and neutralize malicious software, protecting your devices from damage and unauthorized control.
Malware Detection and Response
The ever-evolving threat landscape necessitates a proactive approach to malware detection and response. Our comprehensive solution empowers your enterprise with the tools and expertise required to safeguard your critical data and systems against the most insidious cyberattacks. By leveraging cutting-edge technologies and tailored strategies, we provide unparalleled protection from malware incursions, ensuring business continuity and safeguarding your digital assets.
Enhanced Ransomware Protection
Protect your data from malicious actors with our cutting-edge ransomware protection features.
Ransomware attacks can leave your business vulnerable, encrypting your crucial files and demanding a ransom for their recovery. Our robust safeguards are designed to detect and block these attacks before they can impact your organization.
Our comprehensive solution includes:
Threat Hunting and Investigation
In today's ever-evolving cybersecurity landscape, threat hunting and investigation are crucial to safeguarding your organization's systems and data. This process helps identify malicious activity that may evade traditional security controls, allowing you to respond swiftly and effectively to potential threats.
Through proactive monitoring and advanced analytics, threat hunters analyze security logs, system events, and other data sources to detect suspicious patterns and anomalies. By uncovering hidden threats, they provide early warning signs of a potential attack, enabling prompt remediation and minimizing the impact on your organization.
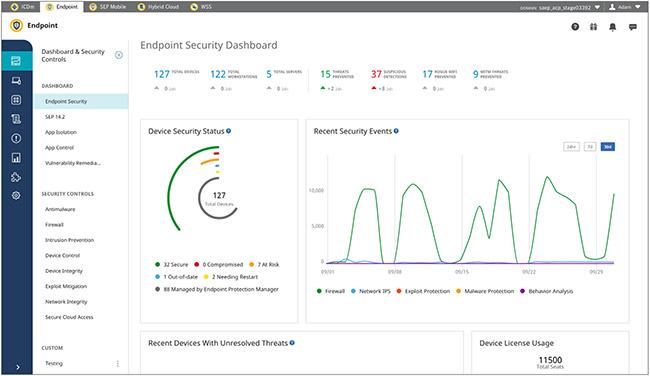
Endpoint Visibility and Control
In today's complex IT landscape, maintaining visibility and control over endpoint devices is paramount. Our comprehensive solution provides you with the tools to achieve this, empowering you to safeguard your organization against cyber threats and ensure seamless operations.
Enhanced Visibility:
Gain a comprehensive view of all endpoint devices connected to your network. Track their activities, vulnerabilities, and compliance status to proactively identify potential risks. Our intuitive dashboard provides real-time insights, allowing you to make informed decisions to protect your infrastructure.
Granular Control:
Take complete control over endpoint devices to enforce security policies, manage access rights, and prevent unauthorized activities. Our advanced control features enable you to remotely lock, wipe, or quarantine compromised devices, minimizing the impact of security breaches.
Risk and Vulnerability Management
In today's complex and ever-evolving cyberthreat landscape, it's imperative to have a robust strategy for identifying, assessing, and mitigating potential risks and vulnerabilities within your organization. Our comprehensive Risk and Vulnerability Management solution provides you with the tools and expertise necessary to stay ahead of threats and protect your critical assets.
Early Detection and Proactive Response
Our solution enables you to proactively identify and prioritize risks by continuously monitoring your systems and networks for potential threats. By detecting vulnerabilities early on, you can take timely action to address them before they become exploited by malicious actors.
Expert Guidance and Tailored Solutions
Our team of security experts will work alongside you to develop a tailored Risk and Vulnerability Management plan that meets your unique requirements. With their extensive experience in threat analysis and mitigation, they will provide in-depth insights and practical guidance to help you make informed decisions and strengthen your security posture.
Cloud-Based Management and Visibility
Centralized Control for Enhanced Security
Unify your security ecosystem with a cloud-based management platform that provides a centralized view of your IT infrastructure. Real-time monitoring and threat intelligence allow you to identify and respond to threats promptly, ensuring the integrity of your systems.
Live Threat Detection and Response
Gain immediate visibility into security events and take swift action with automated threat response capabilities. Monitor suspicious activities in real-time, investigate incidents, and deploy targeted defenses to prevent further damage.
Easy Deployment and Integration
Implementing cybersecurity measures shouldn't be a hassle. Enjoy seamless deployment and effortless integration with our innovative solutions. Designed for ease of use, our platform seamlessly aligns with existing IT infrastructure, minimizing disruption and maximizing efficiency.
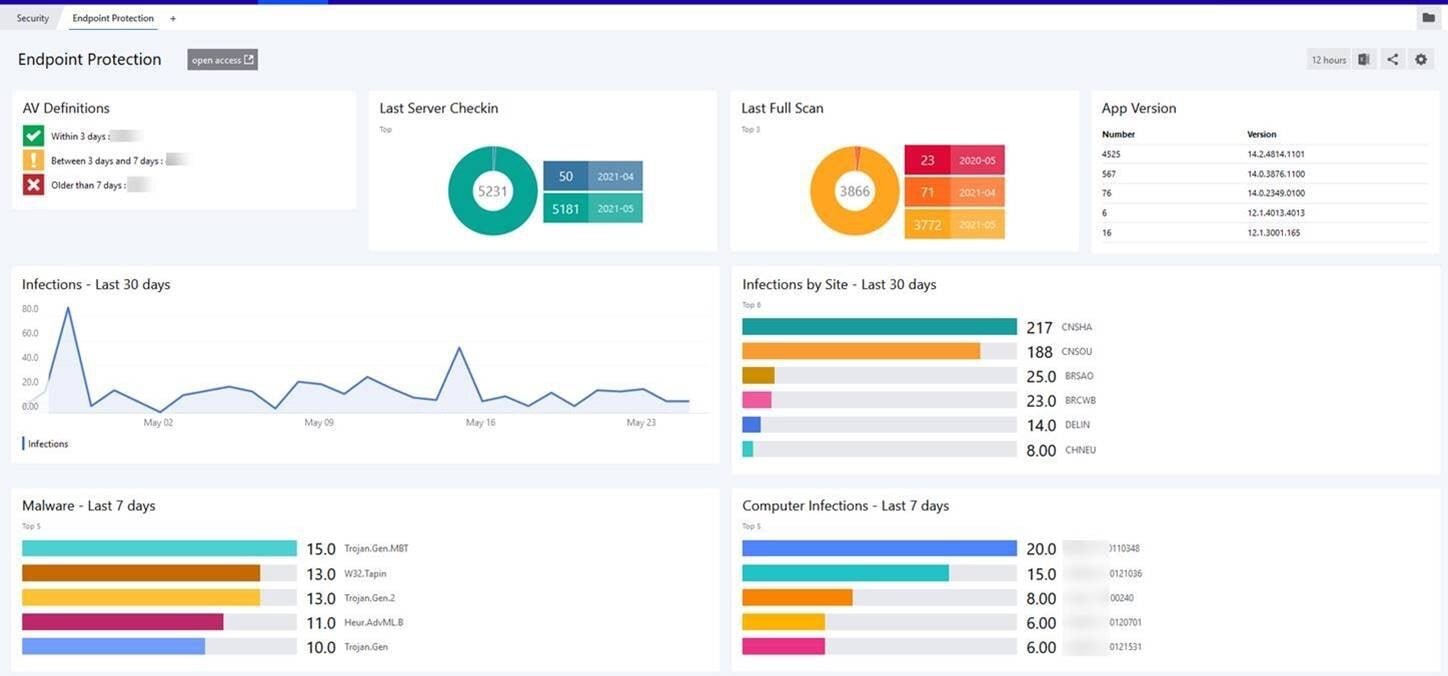
Powerful Reporting and Analytics
Delve deeper into your organization's security posture with comprehensive reporting and analytics. Our solution empowers you to:
Granular Visibility and Control
Generate detailed reports on security events, threats, and agent information. Drill down into specific incidents to understand the root cause and impact. Customized dashboards provide real-time insights into security metrics.
Trend Analysis and Predictive Insights
Identify patterns and trends in your security data to anticipate future risks. Proactive threat detection based on anomaly detection and machine learning. Receive actionable recommendations for enhancing security posture.
Empower your team with the data-driven intelligence to optimize security operations and mitigate risks effectively.