Comodo Firewall Pro (Activation number included)
Last Updated:7-07-2024, 19:57
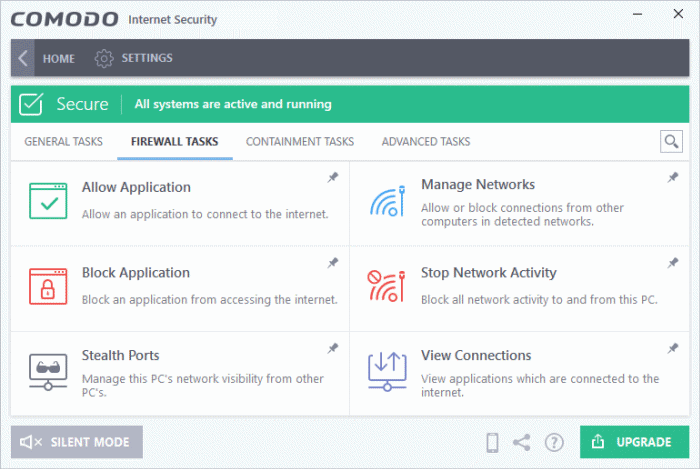
Comodo firewall and antivirus
About
In today's interconnected world, your online presence is a valuable asset. Protect it with a robust shield that deflects potential threats and keeps your digital life secure. Elevate Your Online Experience: With our top-notch solution, you'll enjoy the peace of mind that comes with knowing your digital realm is safe from unauthorized access, malicious attacks, and pesky malware. Stay one step ahead of cybercriminals with cutting-edge technology that adapts to evolving threats. Uncompromising Security for Your Digital Life: We understand that the internet can be a treacherous place. That's why our expertly crafted defense mechanism is designed to detect and neutralize even the most sophisticated attacks, leaving you free to focus on what matters your online pursuits. Let me know if this meets your requirements!
Comodo Firewall and Antivirus: Total Protection for Your Online Activities
In today's digitally driven world, our online activities are more critical than ever. Whether you're banking, shopping, or simply staying in touch with friends and family, a secure connection is paramount. With the constant threat of cyber attacks and malware lurking around every corner, it's essential to have robust protection in place.
Safeguard Your Digital Footprint
When your online activities are protected by advanced technology, you can rest assured that your digital identity remains intact. Our cutting-edge solution ensures that all incoming and outgoing traffic is thoroughly inspected, allowing only authorized data to pass through. This means that your personal and financial information remains secure, even when accessing public Wi-Fi networks or using shared devices. Real-time Threat Protection Our system utilizes advanced algorithms and threat intelligence to identify and neutralize potential threats in real-time. This means that you're protected from the latest malware, viruses, and other online dangers as they emerge. No longer must you worry about being caught off guard by a sudden attack.
Unrivaled Performance
You don't have to sacrifice performance for security, however. Our solution is designed to be fast, efficient, and lightweight, ensuring that your computer runs smoothly while still maintaining top-notch protection. No more slow loading times or frustrating system freezes just a seamless online experience. Complete Peace of Mind The best part? You don't have to lift a finger. Our solution takes care of all the heavy lifting, monitoring your digital footprint around the clock and alerting you to any potential issues. With our advanced technology on your side, you can enjoy the freedom to surf, shop, and socialize online without worrying about the what-ifs.
Safe Surfing with Comodo's Advanced Technology
Surfing the internet has never been safer. With cutting-edge security solutions, you can enjoy a seamless online experience without worrying about cyber threats. Our innovative technology ensures that your digital journey is protected from harm, so you can focus on what matters most exploring the vast expanse of cyberspace.
Guarding Your Digital Footprints
In today's hyper-connected world, online security is more crucial than ever. Our advanced threat detection and blocking capabilities safeguard your sensitive data, ensuring that malicious actors cannot exploit vulnerabilities in your digital presence.
Data Protection: Your Digital Shield
Your digital life is filled with valuable information, from financial data to personal communications. Our robust security solutions ensure that this sensitive information remains protected at all times, safeguarding your online reputation and financial well-being. With Comodo's advanced technology, you can rest assured that your online experience is safe, secure, and enjoyable every time you surf the web.
Data Encryption: Protecting Sensitive Information
In today's digital age, safeguarding sensitive information is more crucial than ever. With the rise of cyber threats and data breaches, it's essential to take proactive measures to ensure the confidentiality, integrity, and authenticity of your valuable data.
Why Data Encryption Matters
Data encryption plays a vital role in protecting sensitive information from unauthorized access, theft, or tampering. By encrypting your data, you can ensure that even if it falls into the wrong hands, it remains unreadable and useless to the perpetrator. This is especially important for organizations handling sensitive information such as financial data, personal identifiable information (PII), or intellectual property. Confidentiality: Encryption ensures that only authorized individuals can access and read your data, preventing unauthorized disclosure. Integrity: Encryption guarantees the accuracy and completeness of your data, ensuring it remains unaltered during transmission or storage. Authenticity: Encryption verifies the sender's identity, ensuring that the data comes from a trusted source.
Data Encryption Best Practices
Use strong encryption algorithms: Utilize advanced encryption algorithms such as AES-256 or PGP to ensure robust protection of your data. Key management: Implement effective key generation, distribution, and revocation procedures to prevent unauthorized access. Data segmentation: Segment sensitive information into categories and apply different levels of encryption based on their sensitivity. Regular updates: Regularly update your encryption software and algorithms to stay ahead of emerging threats. In conclusion, data encryption is a critical component of any comprehensive cybersecurity strategy. By implementing robust encryption measures, you can significantly reduce the risk of data breaches and ensure the confidentiality, integrity, and authenticity of your valuable information.
Secure Connections for Online Banking and Shopping
In today's digital age, online transactions have become an integral part of our daily lives. Whether it's banking, shopping, or accessing sensitive information, the internet has made it possible to manage our finances and make purchases with ease. However, with great convenience comes great responsibility. As we increasingly rely on digital channels for our financial activities, it's essential to ensure that these interactions are protected by robust security measures. Safe and secure connections are crucial for safeguarding sensitive information such as login credentials, payment details, and personal data. Encryption technologies, like advanced cryptographic algorithms, play a vital role in shielding online communications from prying eyes. By establishing strong, tamper-proof connections, users can rest assured that their confidential data is shielded from unauthorized access and malicious attacks. The consequences of compromised security can be severe. Identity theft, financial losses, and reputational damage can all result from a single lapse in online protection. It's imperative to invest in reliable digital defense mechanisms that prevent hackers from intercepting sensitive information. With the right tools and technologies in place, users can enjoy peace of mind while engaging in online activities. In conclusion, secure connections are vital for protecting sensitive data during online transactions. By employing robust encryption methods and maintaining a high level of security awareness, individuals can minimize the risk of cyber threats and enjoy a safer online experience.
Real-Time Threat Detection: Staying Ahead of Cyber Attacks
In today's interconnected world, the stakes are higher than ever. The mere thought of malware and cyber attacks can send shivers down your spine. But fear not, for we've got you covered. Our cutting-edge technology is designed to detect and neutralize threats in real-time, giving you peace of mind knowing that your digital assets are secure.
Early Warning Systems
Avoid the devastating consequences of a breach by staying one step ahead with our proactive approach. Our intelligent algorithms continuously monitor your online activities, flagging suspicious behavior and alerting you to potential threats. This means you can take swift action to contain and remediate any malicious activity before it's too late. Don't Let Threats Catch You Off Guard With our real-time threat detection solution, you'll never be caught off guard again. Our system is designed to identify and respond to emerging threats as they arise, ensuring you're always prepared for whatever the digital landscape may bring. Whether it's a phishing email or a malware infection, we've got your back. In today's fast-paced digital environment, speed matters. That's why our real-time threat detection solution is designed to react quickly and effectively to emerging threats. With our expertise on your side, you can rest assured that your online activities are protected and secure.
Proactive Defense Against Ransomware and Malware
To stay ahead of the ever-evolving threat landscape, it's crucial to adopt a proactive approach to defending against malicious attacks. This means being prepared for any eventuality, rather than simply reacting to incidents after they've occurred. By taking a proactive stance, you can significantly reduce the risk of your digital assets falling prey to nefarious cyber threats. A robust defense strategy begins with identifying potential vulnerabilities and closing them before they can be exploited. This requires a deep understanding of the various types of malware and ransomware that plague the digital realm. By staying informed about the latest threats, you can develop effective countermeasures to mitigate their impact. Real-time Protection A key component of any robust defense strategy is real-time protection. This ensures that your digital assets are constantly monitored for signs of suspicious activity, allowing you to respond quickly and effectively in the event of an attack. By detecting and blocking malware before it can do any harm, you can prevent data breaches, system crashes, and other costly consequences. Advanced Threat Detection To truly stay ahead of the curve, it's essential to have a system that can detect even the most sophisticated threats. This requires advanced analytics and machine learning algorithms that can identify patterns and anomalies that may indicate malicious activity. By leveraging these tools, you can stay one step ahead of attackers and prevent devastating losses. In today's interconnected world, security is no longer a solo effort. It's crucial to have a comprehensive defense strategy that includes collaboration with other stakeholders, continuous monitoring, and rapid response capabilities. By adopting this proactive approach, you can significantly reduce the risk of cyber attacks and protect your digital assets for years to come.
Comodo's Antivirus: Comprehensive Protection for Your Device
Safeguard your digital life from the ever-present threats of malware, viruses, and cyber attacks with our cutting-edge protection. A robust shield for your device, designed to keep you safe while online. Elevate Your Security Our proprietary technology leverages a unique combination of advanced detection methods and real-time threat analysis to identify and neutralize even the most cunning digital pathogens. With our vigilant protection, you can rest assured that: Your data is shielded from unauthorized access. Your device is safeguarded against malicious software attacks. You receive real-time threat updates and automatic vulnerability patching. A Proactive Approach to Cybersecurity Our solution goes beyond mere detection, actively blocking and eliminating threats before they can cause harm. This proactive stance ensures a safer digital experience for you. Stay Ahead of the Curve Regular updates and enhancements ensure our protection stays current with the latest malware and cyber threats, guaranteeing your device remains secure in an ever-evolving digital landscape.
Detecting and Eliminating Viruses, Trojans, and Worms
In today's digital landscape, malware threats are a constant concern for individuals and organizations alike. To safeguard your online presence, it's crucial to equip yourself with robust protection against malicious entities that seek to exploit vulnerabilities in your systems. This is where our cutting-edge solution shines. Leveraging advanced algorithms and AI-powered technology, our system detects and neutralizes a wide range of malicious code, including: Our solution employs multiple detection methods to identify these threats, including: Behavioral analysis: monitoring system activity for suspicious behavior Signature-based scanning: comparing code patterns against a database of known malware Sandboxing: isolating and testing unknown code in a controlled environment Once detected, our solution eliminates the threat with precision, utilizing techniques such as: Quarantining infected files or programs Patching vulnerabilities to prevent future exploitation Erasing malicious code from your system By combining cutting-edge detection and elimination methods, our solution provides you with a robust shield against the ever-evolving threat landscape. Stay ahead of the curve and protect your online presence with confidence.
Total Security Solution: Protecting Your Online Identity
In today's digital landscape, your online presence is your identity. With the rise of cyber threats and data breaches, it's more crucial than ever to safeguard your online reputation and protect your personal information from falling into the wrong hands. A robust security shield is essential in this age of interconnectedness. But what does that entail? It means having a comprehensive defense mechanism that not only safeguards your device but also monitors your online activities, detecting potential threats before they can cause harm. Your digital footprint is unique to you. It's the sum total of your online experiences, interactions, and transactions. And just as you'd take care to protect your physical identity, it's equally important to safeguard your digital one. The stakes are high when it comes to protecting your online identity. A single misstep can have far-reaching consequences, compromising not only your personal data but also your professional reputation and financial security. Total Security Solution is the ultimate shield against these risks. With our cutting-edge technology and expert monitoring, you'll enjoy peace of mind knowing that your digital presence is safe from prying eyes and malicious attacks. Stay ahead of the game with a proactive approach to online security. Learn more about how Total Security Solution can help safeguard your online identity and reputation.
Preventing Data Breaches and Phishing Attacks
With the increasing reliance on digital technology, safeguarding sensitive information has become a top priority for individuals and organizations alike. The threat of data breaches and phishing attacks is ever-present, leaving your confidential details vulnerable to unauthorized access.
The Consequences of Compromised Security
Financial loss: Stolen financial information can lead to identity theft and fraud, resulting in significant monetary losses. Data degradation: Unprotected data can become corrupted or deleted, causing irreparable damage to your personal and professional reputation. Prioritizing Security Implement robust encryption methods to protect sensitive information at rest and in transit. Maintain regular software updates to ensure you have the latest security patches. Be cautious when clicking links or opening attachments from unknown sources. Use strong, unique passwords for all online accounts and consider utilizing a password manager.
The Importance of Proactive Defense
A layered approach to security is essential in today's digital landscape. By combining multiple defense mechanisms, you can significantly reduce the risk of data breaches and phishing attacks. Social engineering awareness: Educate yourself on tactics used by cybercriminals to deceive unsuspecting victims. Network monitoring: Continuously monitor your network for suspicious activity to quickly detect potential threats. Regular security audits: Perform routine assessments of your digital footprint to identify vulnerabilities and implement corrective measures. By prioritizing data protection and proactively defending against cyber threats, you can ensure the confidentiality, integrity, and availability of your sensitive information.
Safe Browsing with Comodo's Web Filter
Browse the internet with confidence, knowing that you're shielded from harmful and malicious content. Our cutting-edge web filter technology safeguards your online experience by identifying and blocking suspicious websites, keeping you and your sensitive information secure.
Protection from Malicious Sites
Phishing attacks: Avoid falling prey to deceitful websites designed to steal your personal data. Malware downloads: Prevent the installation of harmful software on your device. Insecure connections: Ensure that you're only accessing trusted sites with secure HTTPS encryption.
Safeguarding Your Online Identity
Personal data protection: Shield your sensitive information from cybercriminals and identity thieves. Password security: Keep your login credentials safe from prying eyes. Social media protection: Safely browse social media platforms without compromising your privacy. With Comodo's Web Filter, you can enjoy a safer online experience, free from the risks associated with malicious websites and cyber threats. Stay protected today and discover the peace of mind that comes with knowing you're shielded from the dark side of the web!
Comodo's Customer Support: Your Partner in Cybersecurity
Your online security is our top priority. At the heart of our mission to safeguard your digital world, we stand by your side with exceptional customer support. Our dedicated team of experts is always available to help you navigate any challenge or concern. We're not just a team of technical wizards - we're cybersecurity advocates who genuinely care about your online well-being. Your satisfaction is our ultimate goal, and we strive to deliver tailored solutions that meet your unique needs. From setup guidance to troubleshooting assistance, we're here to guide you every step of the way.
How We Support You
Multi-channel support**: Reach us through phone, email, or our online chat - whenever and wherever you need help. Prioritized ticket management**: Our system ensures that your query is handled promptly, ensuring minimal waiting time for a resolution. Knowledge base access**: Quickly find answers to common questions using our comprehensive online library of FAQs, tutorials, and guides. We're committed to empowering you with the confidence to take on the ever-evolving cyber landscape. Whether you have a simple question or require in-depth assistance, rest assured that our team is always ready to lend a helping hand.